Utilizing this type of structured documentation offers several advantages. It helps organizations manage risk effectively by providing a detailed roadmap for identifying and addressing security vulnerabilities. It also fosters transparency and accountability by clearly defining roles, responsibilities, and expected outcomes. Furthermore, a well-defined framework allows for accurate budgeting and resource allocation, leading to better cost control and improved return on investment for security testing efforts.
The following sections will delve deeper into the key components of this crucial planning document, offering practical guidance on its creation and implementation. Specific topics include defining the scope of work, outlining deliverables, establishing timelines and milestones, and addressing legal and contractual considerations.
1. Scope Definition
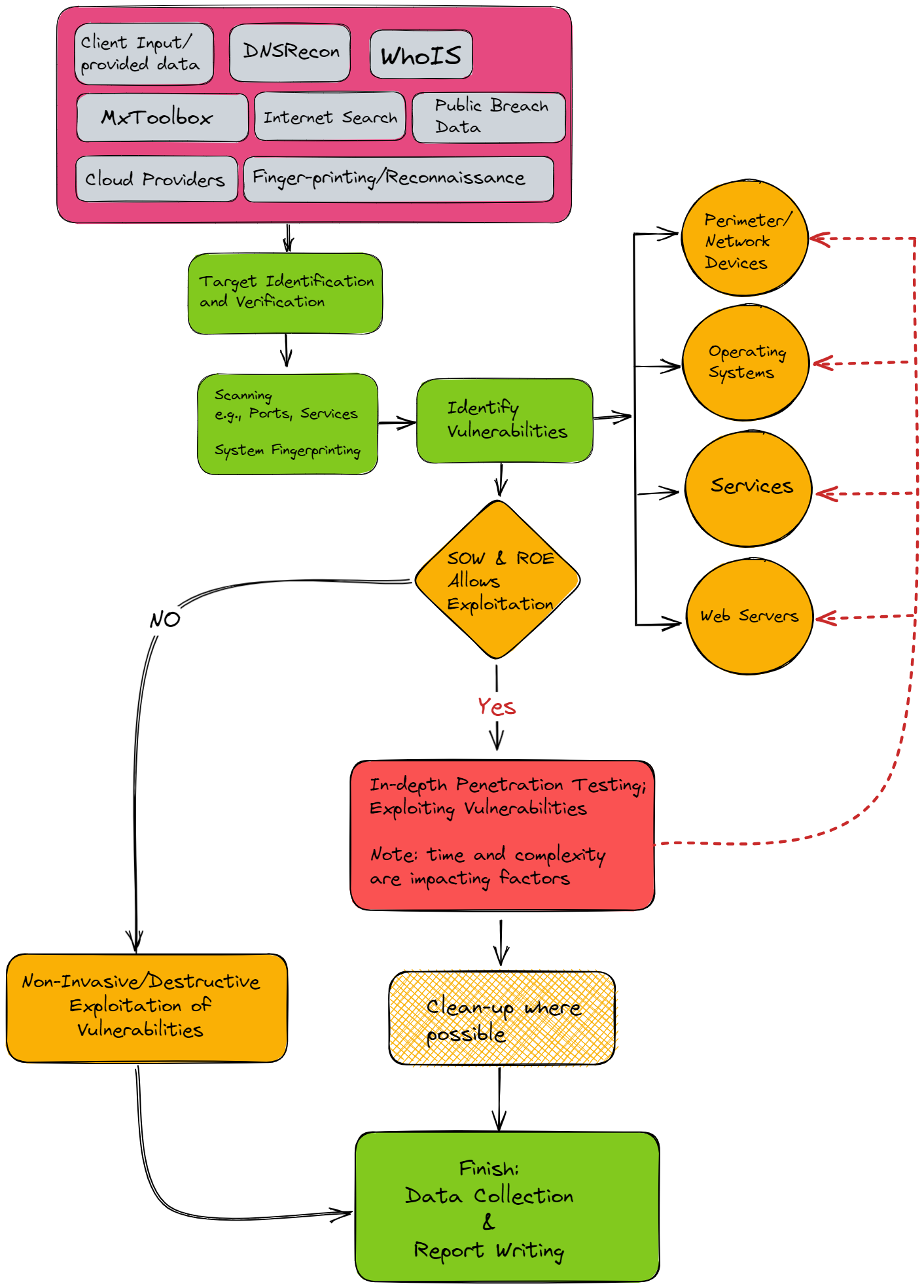
Scope definition forms the cornerstone of a robust penetration testing statement of work. A precisely defined scope ensures that the security assessment focuses on the relevant systems and applications, maximizing the effectiveness of the penetration test while managing costs and timelines. Without a clear scope, testing efforts can become diffuse, leading to wasted resources and potentially overlooking critical vulnerabilities. A well-defined scope clarifies the boundaries of the test, specifying the target systems, networks, or applications included. It also outlines what is explicitly excluded from the assessment. This prevents ambiguity and ensures that all parties are aligned on the objectives and limitations of the penetration test.
Consider an organization commissioning a penetration test. A vaguely defined scope stating “test the network” leaves significant room for interpretation. Does this include all internal networks? External-facing systems? Third-party connections? A precisely defined scope, however, might specify “test the external perimeter of the corporate network, including the web application at www.example.com and the customer portal API.” This level of detail ensures the testers focus their efforts on the most critical assets, delivering actionable results within the allocated budget and timeframe. Conversely, a poorly defined scope can result in disputes over deliverables, unexpected costs, and ultimately, an incomplete understanding of the organization’s security posture.
Precise scope definition facilitates accurate resource allocation, realistic scheduling, and meaningful reporting. It allows penetration testers to develop tailored testing strategies and select appropriate tools and techniques. This precision translates to more efficient testing, higher-quality findings, and ultimately, a more secure environment. Challenges in defining scope often stem from a lack of understanding of the organization’s own IT infrastructure or unclear security objectives. Addressing these challenges requires thorough internal communication and collaboration between IT, security, and business stakeholders to establish a shared understanding of the systems requiring assessment and the desired outcomes of the penetration test. This collaborative approach leads to a more effective and valuable security assessment, aligning security efforts with business priorities and maximizing the return on investment in penetration testing.
2. Testing Methodology
The testing methodology section within a penetration testing statement of work serves as a critical blueprint, dictating the specific tactics and techniques employed during the security assessment. This section bridges the gap between the defined scope and the delivered results, ensuring the penetration test aligns with industry best practices and addresses the organization’s unique security concerns. Articulating the chosen methodology fosters transparency and allows stakeholders to understand the rigor and depth of the testing process. This clarity also enables informed decision-making based on the identified vulnerabilities and subsequent recommendations.
Several recognized methodologies exist, each offering a distinct approach to penetration testing. Examples include the Open Web Application Security Project (OWASP) Testing Guide, the National Institute of Standards and Technology (NIST) Special Publication 800-115, and the Penetration Testing Execution Standard (PTES). Selecting the appropriate methodology depends on factors such as the target environment, regulatory requirements, and the organization’s specific security objectives. For instance, a financial institution undergoing a compliance-driven penetration test might mandate adherence to NIST guidelines, while a startup assessing a web application might opt for the OWASP framework. Specifying the chosen methodology within the statement of work ensures all parties understand the testing approach and its implications for the final report.
Clearly defining the testing methodology within the statement of work provides numerous benefits. It enables accurate scoping and resource allocation, as different methodologies require varying levels of effort and expertise. It also facilitates consistent and repeatable testing processes, allowing for meaningful comparisons across multiple assessments. Furthermore, a well-defined methodology fosters trust and confidence in the results, demonstrating a commitment to industry standards and best practices. However, challenges can arise if the chosen methodology is not properly documented or if the testing team deviates from the agreed-upon approach. Therefore, meticulous documentation and adherence to the defined methodology are crucial for a successful and impactful penetration test. This meticulousness ensures the results accurately reflect the organization’s security posture and provide a reliable basis for remediation efforts.
3. Deliverables (Reports)
The “Deliverables (Reports)” section within a penetration testing statement of work holds significant weight, outlining the tangible outcomes of the assessment. This section directly connects the executed testing methodology to actionable insights for the organization. A clearly defined deliverables section ensures that the penetration testing engagement produces the necessary documentation to understand identified vulnerabilities, assess their potential impact, and guide remediation efforts. Without specific and well-defined deliverables, the value of the penetration test diminishes, potentially leaving the organization with incomplete information and an unclear path forward. The deliverables section functions as a contractual agreement on the information provided upon completion of the testing phase.
Typical deliverables within a penetration testing engagement include a comprehensive technical report detailing identified vulnerabilities, their severity levels, and recommended mitigation strategies. This report often includes proof-of-concept exploits demonstrating the potential impact of vulnerabilities. An executive summary provides a high-level overview of the findings, allowing non-technical stakeholders to grasp the key security risks. Other potential deliverables might include a prioritized vulnerability list, remediation guidance documents, or retesting reports verifying the effectiveness of implemented fixes. For example, a vulnerability report might detail a SQL injection flaw in a web application, outlining the technical details of the exploit, its potential impact on data confidentiality, and specific steps to remediate the vulnerability. The accompanying executive summary would then highlight the presence of a high-severity vulnerability in the web application, emphasizing the potential for data breaches and the need for immediate action. This tiered approach ensures all stakeholders receive relevant and actionable information.
A well-defined deliverables section fosters clear expectations and accountability between the testing team and the organization. It ensures the provided documentation aligns with the organization’s specific needs and facilitates effective communication of the security assessment’s results. However, challenges can arise if the deliverables are not sufficiently detailed or if they fail to address the organization’s key security concerns. Ambiguity within the deliverables section can lead to disputes, delays, and ultimately, a less impactful security assessment. Therefore, meticulous planning and clear communication regarding expected deliverables are paramount to a successful penetration testing engagement. This clarity maximizes the value derived from the penetration test, providing the organization with the necessary information to strengthen its security posture effectively.
4. Timeline and Milestones
Within a penetration testing statement of work, the “Timeline and Milestones” section provides a crucial roadmap for the engagement, outlining the expected duration and key checkpoints throughout the process. This section establishes a shared understanding of the project’s temporal boundaries, facilitating effective resource allocation, progress tracking, and timely completion. A well-defined timeline ensures the penetration test aligns with organizational schedules and minimizes disruption to ongoing operations. Without a clear timeline and defined milestones, the project risks schedule slippage, potentially impacting budget constraints and delaying critical security improvements.
- Project InitiationThis phase marks the formal commencement of the penetration test, typically involving project kick-off meetings, documentation review, and initial setup. For example, this phase might include a meeting between the penetration testing team and the organization’s security personnel to review the scope of work, discuss logistical details, and establish communication channels. This initial alignment sets the stage for a smooth and efficient testing process. Clear definition of this phase ensures all parties understand their initial responsibilities and sets a collaborative tone for the entire engagement.
- Testing Phase ExecutionThis phase encompasses the core activities of the penetration test, including vulnerability scanning, exploitation attempts, and security analysis. Milestones within this phase might include the completion of specific testing modules, such as network scanning, web application testing, or social engineering exercises. For instance, completing the network scanning milestone would signal the testing team’s progress and readiness to move on to subsequent phases like web application testing. These milestones allow for ongoing monitoring of progress and enable proactive identification of potential delays.
- Reporting and Remediation GuidanceThis phase focuses on documenting the findings of the penetration test and providing actionable recommendations for remediation. Key milestones in this phase might include the delivery of draft reports, review periods for feedback, and the submission of the final penetration testing report. For instance, submitting the draft report milestone allows the organization to review the findings, request clarifications, and validate the identified vulnerabilities before finalization. This iterative feedback process ensures the final report accurately reflects the security assessment and provides actionable insights.
- Retesting and ClosureThis phase often includes optional retesting to validate the effectiveness of implemented remediation measures. Milestones in this phase might involve the completion of retesting procedures and the issuance of a final closure report confirming the resolution of identified vulnerabilities. This validation step ensures the implemented fixes effectively mitigate the identified risks, providing a measurable outcome of the penetration testing engagement. This final step reinforces the value of the penetration test and provides assurance of improved security posture.
A well-defined timeline with specific milestones offers numerous benefits, including improved project management, enhanced communication, and increased accountability. It provides a framework for tracking progress, identifying potential roadblocks, and ensuring the penetration test stays on track and within budget. This structured approach enables proactive management of the engagement, maximizing its effectiveness and minimizing disruptions to the organization’s operations. By clearly outlining the expected timeframe and key deliverables at each stage, the “Timeline and Milestones” section strengthens the overall value and impact of the penetration testing statement of work.
5. Communication Protocols
Effective communication serves as a cornerstone of successful penetration testing engagements. The communication protocols section within a penetration testing statement of work outlines the methods, frequency, and responsible parties for information exchange throughout the assessment. This structured approach ensures timely dissemination of critical information, facilitates efficient collaboration between the testing team and the organization, and minimizes potential misunderstandings. Without clearly defined communication protocols, critical information might be delayed, misconstrued, or overlooked entirely, jeopardizing the effectiveness of the penetration test and potentially delaying remediation efforts.
Establishing designated points of contact within both the testing team and the organization streamlines communication pathways. Regular status updates, delivered through agreed-upon channels such as email, conference calls, or project management platforms, keep stakeholders informed of progress and potential roadblocks. Defining escalation procedures for critical issues ensures timely responses to time-sensitive security concerns. For instance, if a critical vulnerability is discovered during testing, a pre-defined escalation procedure might dictate immediate notification of the organization’s security officer via a direct phone call, followed by a written summary through email. This structured approach ensures prompt attention to high-priority issues and facilitates rapid remediation. Similarly, regular status reports, perhaps delivered weekly via email, keep the organization informed of the testing progress, identified vulnerabilities, and any emerging challenges. This consistent communication fosters transparency and allows the organization to proactively address any concerns or adjust timelines as needed. Documentation of these communication protocols within the statement of work solidifies expectations and ensures accountability.
Clearly defined communication protocols contribute significantly to the success of a penetration test. They facilitate proactive issue management, foster collaborative problem-solving, and ensure timely dissemination of critical information. However, challenges can arise if communication protocols are not adequately documented or followed. Ambiguity in communication channels or escalation procedures can lead to delays, miscommunication, and ultimately, a less effective security assessment. Therefore, meticulous planning and clear documentation of communication protocols within the statement of work are essential. This clarity ensures a smooth, efficient, and ultimately more impactful penetration testing engagement, maximizing the value of the security assessment and enabling the organization to address identified vulnerabilities promptly and effectively. Well-defined communication processes strengthen the partnership between the testing team and the client organization, leading to a more collaborative and productive security engagement.
6. Legal and Compliance
The “Legal and Compliance” section of a penetration testing statement of work holds critical importance, addressing potential legal ramifications and ensuring adherence to relevant regulations. This section safeguards both the organization commissioning the test and the security professionals conducting it. Neglecting legal and compliance considerations can expose both parties to significant risks, including legal action, regulatory penalties, and reputational damage. This section clarifies the boundaries of the testing activities, ensuring they remain within legal and ethical limits. For example, unauthorized access to systems, even for security testing purposes, can violate laws such as the Computer Fraud and Abuse Act (CFAA). Therefore, explicit authorization from the system owner is crucial, documented within the statement of work.
Data protection regulations, such as GDPR, CCPA, or HIPAA, impose strict requirements on handling sensitive information. The statement of work must address these requirements, outlining how data will be handled during the penetration test, stored, and ultimately disposed of. For instance, if a penetration test involves accessing systems containing protected health information (PHI), the statement of work should explicitly state adherence to HIPAA regulations, including data encryption, secure storage, and limited access provisions. Furthermore, intellectual property rights and confidentiality agreements protect sensitive information disclosed during the engagement. These agreements, outlined within the legal and compliance section, ensure that confidential information remains protected and is not misused or disclosed without proper authorization. Addressing these legal and regulatory aspects within the statement of work builds trust and transparency between the parties involved.
Inclusion of robust legal and compliance provisions in the statement of work mitigates risk and fosters a responsible security assessment. It ensures adherence to legal and ethical standards, protecting both the organization and the testing team from potential legal challenges. Challenges can arise if legal and compliance aspects are not adequately addressed. Ambiguity or omissions in this section can lead to legal disputes, regulatory fines, and reputational harm. Therefore, meticulous attention to detail and clear articulation of legal and compliance requirements are essential for a successful and legally sound penetration testing engagement. This proactive approach demonstrates a commitment to responsible security practices and fosters trust between all parties involved. It ensures that the penetration test not only identifies vulnerabilities but also adheres to the highest legal and ethical standards, ultimately contributing to a more secure and compliant environment.
Key Components of a Penetration Testing Statement of Work
A comprehensive penetration testing statement of work requires careful consideration of several key components. These components ensure clarity, manage expectations, and contribute to a successful security assessment.
1. Scope Definition: Precisely defines the target systems, applications, and networks included in the assessment, as well as those explicitly excluded. This clarity ensures focused testing efforts and avoids scope creep.
2. Testing Methodology: Specifies the approach and techniques used during the penetration test, ensuring alignment with industry best practices and addressing the organization’s unique security concerns. Referencing established frameworks like OWASP or NIST provides a structured approach.
3. Deliverables (Reports): Outlines the expected documentation, such as vulnerability reports, executive summaries, and remediation guidance, providing tangible outcomes and actionable insights.
4. Timeline and Milestones: Establishes a clear project timeline with defined milestones, facilitating progress tracking, resource allocation, and timely completion. This structure helps manage expectations and ensure the project remains on schedule.
5. Communication Protocols: Specifies communication channels, frequency of updates, designated points of contact, and escalation procedures. This clarity ensures efficient information flow and prompt attention to critical issues.
6. Legal and Compliance: Addresses legal considerations, data protection regulations, intellectual property rights, and confidentiality agreements, ensuring the penetration test adheres to legal and ethical standards.
These components, when clearly defined and documented within the statement of work, contribute significantly to a successful and impactful penetration test. They ensure a shared understanding between the organization and the testing team, facilitating a smooth, efficient, and legally sound security assessment. This structured approach maximizes the value of the penetration test, providing the organization with the necessary information and insights to strengthen its security posture effectively.
How to Create a Penetration Testing Statement of Work
Creating a robust penetration testing statement of work (SOW) requires careful planning and attention to detail. A well-structured SOW ensures clarity, manages expectations, and sets the stage for a successful security assessment. The following steps outline a structured approach to developing a comprehensive penetration testing SOW.
1. Define the Scope: Clearly articulate the systems, applications, and networks included in the assessment. Specify IP ranges, hostnames, and web application URLs. Explicitly state any exclusions to avoid ambiguity.
2. Outline Objectives: Specify the goals of the penetration test. Examples include identifying vulnerabilities, assessing exploitability, or validating security controls. Clearly defined objectives focus the testing efforts and ensure alignment with organizational security goals.
3. Select the Testing Methodology: Choose an appropriate methodology based on the target environment and objectives. Common methodologies include OWASP, NIST, and PTES. Documenting the chosen methodology ensures transparency and rigor.
4. Specify Deliverables: Clearly define the expected documentation, including vulnerability reports, executive summaries, remediation guidance, and retesting reports. Specify the format, content, and delivery timelines for each deliverable.
5. Establish a Timeline: Develop a realistic project timeline with defined milestones. Include key dates for project initiation, testing phases, reporting, and retesting. A well-defined timeline facilitates progress tracking and resource management.
6. Define Communication Protocols: Establish clear communication channels, reporting frequency, points of contact, and escalation procedures. This structure ensures timely and efficient communication throughout the engagement.
7. Address Legal and Compliance Requirements: Outline legal considerations, data protection regulations, intellectual property rights, and confidentiality agreements. Ensuring legal compliance protects both the organization and the testing team.
8. Review and Finalize: Thoroughly review the SOW with all stakeholders, including the organization’s security team and the penetration testing team. Ensure all parties agree on the scope, objectives, deliverables, timeline, and legal considerations. Finalize the document and obtain necessary approvals before commencing the penetration test.
A comprehensive penetration testing SOW, incorporating these key components, forms the foundation of a successful security assessment. This structured approach ensures clarity, manages expectations, and facilitates a collaborative and productive engagement between the organization and the penetration testing team, maximizing the value and impact of the security assessment.
Careful consideration of the elements within this type of document ensures a thorough and effective security assessment. From defining the scope and selecting an appropriate methodology to outlining deliverables and establishing communication protocols, each component plays a vital role in maximizing the value of the penetration test. Addressing legal and compliance requirements safeguards both the organization and the testing team, fostering a responsible and ethical security engagement. A well-defined framework provides a roadmap for identifying vulnerabilities, assessing their potential impact, and implementing effective remediation strategies. This structured approach enables organizations to strengthen their security posture, protect sensitive data, and maintain the trust of their stakeholders.
Organizations must recognize that security is not a static target but a continuous process of improvement. Regular penetration testing, guided by a robust and comprehensive planning document, provides invaluable insights into evolving security risks. Investing in proactive security measures, such as penetration testing, demonstrates a commitment to protecting valuable assets and maintaining a strong security posture. This proactive approach, combined with a clear understanding of the organization’s unique security landscape, is essential for navigating the complex and ever-changing threat landscape. Ultimately, a well-defined approach to penetration testing empowers organizations to make informed decisions about their security investments and build a more resilient and secure environment.