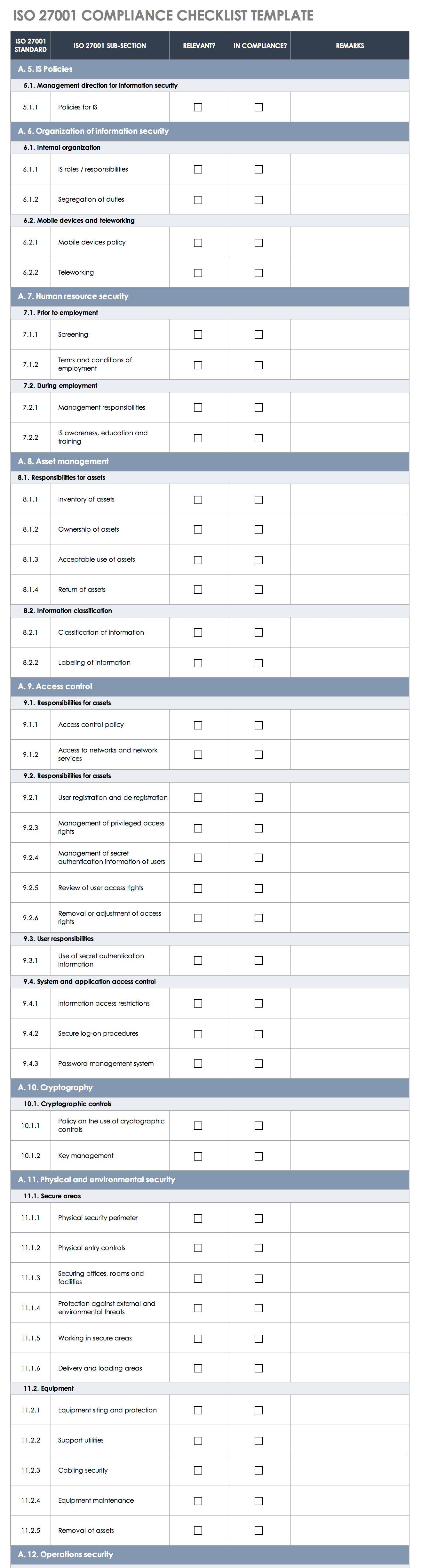
Using a predefined structure aids in consistent and comprehensive documentation. This ensures all necessary controls are considered, reducing the risk of overlooking critical security aspects. It simplifies the audit process by offering a clear overview of the ISMS scope and implemented controls. Furthermore, it helps organizations demonstrate their commitment to information security and facilitates continuous improvement by providing a baseline for future reviews and updates.
The following sections will delve deeper into specific elements and practical examples, offering guidance on developing and implementing an effective document aligned with ISO/IEC 27001 requirements. Topics covered will include control selection rationale, implementation details, and best practices for maintenance and review.
1. Control Selection
Control selection forms the core of a Statement of Applicability (SOA) within the ISO/IEC 27001 framework. A well-defined SOA hinges on a meticulous selection process, ensuring appropriate security controls are implemented to address specific organizational risks and vulnerabilities. This process directly impacts the effectiveness of the information security management system (ISMS).
- Risk Assessment ResultsControl selection must be driven by a thorough risk assessment. The identified risks and vulnerabilities inform the choice of controls necessary for mitigation. For example, if a risk assessment reveals a high vulnerability to phishing attacks, controls related to security awareness training and email filtering become crucial. The SOA justifies these choices by directly referencing the risk assessment results.
- Applicability to the OrganizationNot all controls within Annex A of ISO/IEC 27001 are relevant to every organization. The selection process involves determining which controls are applicable based on specific organizational circumstances, legal requirements, and industry best practices. For instance, a small business might deem certain physical security controls, designed for large data centers, inapplicable. This rationale should be clearly documented within the SOA.
- Feasibility of ImplementationControl selection considers practical constraints, such as budget, resources, and technical capabilities. While a specific control might be deemed necessary, its implementation might be deferred due to resource limitations. The SOA should reflect this decision, outlining planned implementation timelines and justifying any delays. This transparency ensures accountability and supports continuous improvement.
- Legal and Regulatory RequirementsCompliance with applicable laws and regulations influences control selection. Organizations operating in specific sectors, such as finance or healthcare, face stringent regulatory requirements concerning data protection and privacy. The SOA demonstrates compliance by explicitly referencing the relevant regulations and mapping them to the selected controls. This alignment ensures legal adherence and strengthens the overall ISMS.
Effective control selection, guided by risk assessment, organizational context, feasibility, and legal compliance, establishes a robust foundation for the SOA. This, in turn, ensures the ISMS adequately protects sensitive information and supports organizational objectives.
2. Justification
Justification within a Statement of Applicability (SOA) provides the rationale behind control selection and implementation decisions. A clear and comprehensive justification demonstrates due diligence in aligning security controls with organizational risks and regulatory requirements. It serves as a critical component of the ISO/IEC 27001 framework, offering transparency and accountability within the Information Security Management System (ISMS).
- Inclusion RationaleThis aspect explains why specific controls from Annex A are included in the ISMS. Justification often references the results of the risk assessment, highlighting the specific risks or vulnerabilities a control addresses. For example, including the control “Access Control” might be justified by the risk of unauthorized access to sensitive data, as identified in the risk assessment. This clear link between risk and control selection strengthens the SOA’s credibility.
- Exclusion RationaleEqually important is justifying the exclusion of controls. Organizations must explain why certain controls deemed relevant by the standard are not implemented. This might be due to the control’s inapplicability to the organization’s specific context or the presence of alternative mitigating measures. For instance, a company operating entirely in the cloud might exclude physical security controls related to on-premises servers, explaining their reliance on the cloud provider’s physical security measures.
- Implementation Status ExplanationJustification extends to the implementation status of controls. If a control is marked as “planned,” the SOA should explain the implementation timeline and any factors contributing to the delay. For example, budgetary constraints might postpone the implementation of a costly security tool. Transparency regarding planned implementations demonstrates commitment to continuous improvement and allows for tracking progress.
- Reference to Supporting DocumentationStrong justifications often refer to supporting documentation that provides further evidence for the decisions made. This might include risk assessment reports, policy documents, or implementation plans. Linking the SOA to these documents enhances its validity and facilitates audits by providing readily available evidence. For example, referencing a vulnerability scan report can substantiate the need for a specific technical control.
Comprehensive justification within the SOA enhances the ISMS’s overall integrity and demonstrates a commitment to information security best practices. It ensures transparency and facilitates effective communication with stakeholders, including auditors and regulatory bodies. This meticulous approach strengthens the organization’s security posture and fosters trust in its information security management capabilities.
3. Implementation Status
The implementation status within a Statement of Applicability (SOA) provides a clear snapshot of the current state of security controls concerning the ISO/IEC 27001 standard. This status clarifies whether each control from Annex A is implemented, planned for future implementation, or deemed not applicable. Accurate and up-to-date implementation status is crucial for effective ISMS management, audit preparedness, and ongoing improvement.
- Implemented ControlsThis status signifies that a control is fully operational within the organization. Evidence of implementation, such as policy documents, system configurations, and operational procedures, should be readily available. For example, an implemented “access control” policy would be supported by documented procedures, access logs, and system configurations demonstrating its enforcement. Clearly marking implemented controls within the SOA provides assurance of active security measures.
- Planned ControlsThis status indicates controls identified as necessary but not yet operational. The SOA should outline planned implementation dates and rationale for any delays. For example, a “data loss prevention” tool planned for next quarter, due to budgetary constraints, would be marked accordingly. This transparency promotes accountability and enables tracking progress towards full compliance.
- Not Applicable ControlsThis designation applies to controls deemed irrelevant to the organization’s specific context or risk profile. Justification for deeming a control not applicable is critical, often referencing risk assessment results or alternative mitigating measures. For instance, a company operating entirely in the cloud might mark physical security controls for on-premise servers as “not applicable,” citing the cloud provider’s responsibility for physical security.
- Partially Implemented ControlsWhile not explicitly defined in the standard, this status can be useful for organizations in transition. It signifies that certain aspects of a control are in place, while others require further development. For example, a partially implemented “incident response” plan might have established procedures but lack dedicated personnel training. This status allows for nuanced tracking of implementation progress and identifies areas requiring attention.
Accurate implementation status within the SOA offers a vital overview of the ISMS maturity. It facilitates effective communication with stakeholders, supports audit processes, and enables informed decision-making regarding resource allocation and security improvements. Maintaining a current and accurate SOA, reflecting the evolving implementation status of controls, is essential for a robust and successful ISMS.
4. Annex A Mapping
Annex A mapping within a Statement of Applicability (SOA) directly links selected controls to the ISO/IEC 27001 standard’s comprehensive list of controls. This mapping provides a clear, auditable trail demonstrating how an organization addresses each relevant control. It ensures compliance and facilitates a structured approach to information security management.
- Control IdentificationEach control selected for implementation within the ISMS must be explicitly mapped to its corresponding entry in Annex A. This typically involves referencing the control’s unique identifier (e.g., A.5.1.1 – Policies for information security). Clear identification ensures unambiguous referencing and simplifies audits by providing a direct link to the standard’s requirements.
- Justification for SelectionAnnex A mapping reinforces the justification provided for each control. By linking the selected control to its description in Annex A, the SOA clarifies the control’s purpose and its relevance to the organization’s specific risks. For example, selecting control A.8.2.3 – Backup of information can be justified by the risk of data loss due to system failures, directly referencing Annex A’s description of this control.
- Implementation DetailsWhile Annex A provides a general description of each control, the SOA elaborates on implementation specifics. This might include references to specific policies, procedures, or technical configurations that demonstrate how the control is implemented within the organization’s environment. For instance, mapping to control A.9.2.1 – User access management might involve detailing the specific access control software employed and referencing the associated user access policy.
- Status TrackingAnnex A mapping facilitates tracking the implementation status of each control. By maintaining a clear link between the SOA and Annex A, organizations can easily monitor progress towards full implementation and identify any gaps requiring attention. This structured approach supports continuous improvement and ensures the ISMS remains aligned with the standard’s requirements.
Accurate and comprehensive Annex A mapping strengthens the SOA, providing a structured and auditable demonstration of compliance with ISO/IEC 27001. It enhances transparency, simplifies audits, and supports ongoing management and improvement of the ISMS. This meticulous approach fosters confidence in the organization’s information security posture and demonstrates a commitment to best practices.
5. Regular Review
Maintaining an up-to-date Statement of Applicability (SOA) is crucial for an effective Information Security Management System (ISMS) under ISO/IEC 27001. Regular review ensures the SOA accurately reflects the organization’s current security posture, controls, and risk environment. Without periodic review, the SOA risks becoming obsolete, misrepresenting the ISMS’s actual state and potentially leading to non-compliance.
Several factors necessitate regular SOA review. Changes in business operations, such as adopting new technologies or expanding into new markets, can introduce new risks and require adjustments to existing controls or the implementation of new ones. Similarly, evolving threat landscapes and emerging vulnerabilities necessitate continuous evaluation and updates to the SOA. Furthermore, periodic internal audits and management reviews, as mandated by ISO/IEC 27001, provide opportunities to assess the SOA’s effectiveness and identify areas for improvement. For example, an organization migrating its infrastructure to the cloud would need to review and update its SOA to reflect changes in physical security controls and the implementation of cloud-specific security measures. Another example is a company experiencing a significant data breach; this event would trigger a review of the SOA to identify control gaps and implement necessary enhancements.
Regular review, integrated within the broader ISMS management framework, ensures the SOA remains a dynamic and relevant document. It provides a mechanism for continuous improvement, enabling organizations to adapt to changing circumstances and maintain a robust security posture. Failure to conduct regular reviews can lead to an inaccurate and ineffective SOA, increasing the risk of security breaches and non-compliance with ISO/IEC 27001 requirements. A well-maintained SOA, subject to periodic review and updates, demonstrates a commitment to information security best practices and provides a solid foundation for a successful ISMS.
6. Supporting Documentation
Supporting documentation plays a crucial role in validating the claims made within a Statement of Applicability (SOA) for ISO/IEC 27001. It provides evidence of control implementation and the rationale behind security decisions. Without robust supporting documentation, the SOA lacks verifiable substance and cannot effectively demonstrate adherence to the standard’s requirements. This documentation forms the backbone of a credible and auditable ISMS.
- Policies and ProceduresDocumented policies and procedures demonstrate an organization’s commitment to implementing security controls. For example, a password policy document outlining password complexity requirements and regular change intervals supports the implementation of the “password management” control. These documents provide specific instructions and guidelines for employees to follow, ensuring consistent application of security measures.
- Risk Assessment ReportsRisk assessments form the basis for control selection and justification within the SOA. Documented risk assessment reports, detailing identified threats, vulnerabilities, and impact assessments, provide the rationale for chosen controls. For instance, a risk assessment report identifying a high risk of malware infections justifies the implementation of anti-malware software and regular system scans.
- System Configuration DocumentsTechnical configurations demonstrating the implementation of security controls constitute essential supporting documentation. Firewall configuration files, access control lists, and intrusion detection system settings provide verifiable evidence of technical control implementation. These documents validate the SOA’s claims regarding the technical aspects of information security.
- Implementation Plans and RecordsDocumentation related to the planning and implementation of security controls, such as project plans, timelines, and implementation reports, provides further support for the SOA. These documents demonstrate progress towards achieving security objectives and offer evidence of a structured and managed approach to ISMS implementation. They also provide a valuable audit trail, tracking the evolution of the ISMS.
Comprehensive supporting documentation reinforces the validity and credibility of the SOA. It provides tangible evidence of control implementation, enabling auditors and stakeholders to verify the organization’s adherence to ISO/IEC 27001 requirements. This meticulous approach to documentation strengthens the overall ISMS and demonstrates a commitment to robust information security practices. A well-documented SOA, supported by verifiable evidence, forms the foundation of a successful and demonstrably secure information management system.
Key Components of an ISO 27001 Statement of Applicability
A comprehensive Statement of Applicability (SOA) requires careful consideration of several key components. These components ensure clarity, completeness, and alignment with the ISO/IEC 27001 standard.
1. Control Objective: Clearly state the intended outcome of each selected control. This clarifies the control’s purpose within the overall security framework. For example, the objective of access control is to prevent unauthorized access to sensitive information.
2. Control Selection (from Annex A): Identify the specific controls chosen from Annex A of ISO/IEC 27001. Precise referencing (e.g., A.6.1.2) ensures clear mapping to the standard.
3. Justification: Provide a rationale for including or excluding each control. Justifications should reference risk assessment results, organizational context, and legal or regulatory requirements.
4. Implementation Status: Clearly indicate whether a control is implemented, planned, or not applicable. Planned controls should include anticipated implementation dates.
5. Implementation Details: Describe how each implemented control is put into practice. This may include references to specific policies, procedures, technologies, or configurations.
6. Supporting Documentation: Reference any documentation that provides evidence of control implementation, such as policies, procedures, risk assessments, or system configurations.
7. Responsible Party: Identify the individual or team responsible for managing and maintaining each control. This ensures accountability and facilitates communication.
8. Review Frequency: Specify how often each control and the overall SOA will be reviewed and updated. Regular review ensures the SOA remains current and relevant.
A well-structured SOA, encompassing these key components, provides a transparent and auditable overview of an organization’s security controls, demonstrating commitment to information security best practices and facilitating effective ISMS management.
How to Create a Statement of Applicability for ISO 27001
Creating a robust Statement of Applicability (SOA) is crucial for demonstrating compliance with ISO/IEC 27001. A methodical approach ensures completeness and alignment with organizational security needs.
1: Define Scope: Clearly define the scope of the Information Security Management System (ISMS). This clarifies which areas of the organization and which information assets are covered by the SOA.
2: Conduct a Risk Assessment: A thorough risk assessment identifies vulnerabilities and threats to information assets. This assessment informs control selection and justification within the SOA.
3: Select Controls: Based on the risk assessment results, select appropriate controls from Annex A of ISO/IEC 27001. Consider organizational context, feasibility, and legal requirements.
4: Justify Control Selections: Document the rationale for including or excluding each control. Justifications should clearly link controls to identified risks or explain alternative mitigating measures.
5: Determine Implementation Status: Indicate whether each selected control is implemented, planned, or not applicable. Provide planned implementation dates for controls not yet in place.
6: Document Implementation Details: Describe how each implemented control functions within the organization. Reference specific policies, procedures, technologies, and configurations.
7: Gather Supporting Documentation: Compile evidence supporting the implementation of controls. This includes policies, procedures, risk assessment reports, system configurations, and implementation records.
8: Review and Update Regularly: The SOA should be reviewed and updated periodically, especially after changes to business operations, risk assessments, or the threat landscape. This ensures the SOA remains current and accurately reflects the organization’s security posture.
A well-structured SOA, built upon these steps, provides a clear and comprehensive overview of security controls and their implementation status, facilitating effective ISMS management and demonstrating a commitment to information security best practices.
Careful consideration of control selection, justification, implementation status, and supporting documentation are essential for creating a robust and effective document. A well-maintained document, aligned with organizational risks and regularly reviewed, forms a cornerstone of a successful Information Security Management System (ISMS) under ISO/IEC 27001. It provides a clear roadmap for implementing and managing security controls, demonstrating a commitment to protecting sensitive information.
Organizations pursuing or maintaining ISO/IEC 27001 certification must prioritize the development and upkeep of this crucial document. Its significance lies in providing a clear, concise, and auditable representation of the organization’s security posture, paving the way for a robust and demonstrably secure environment.